#include "include/jxmssa.h"
Detailed Description
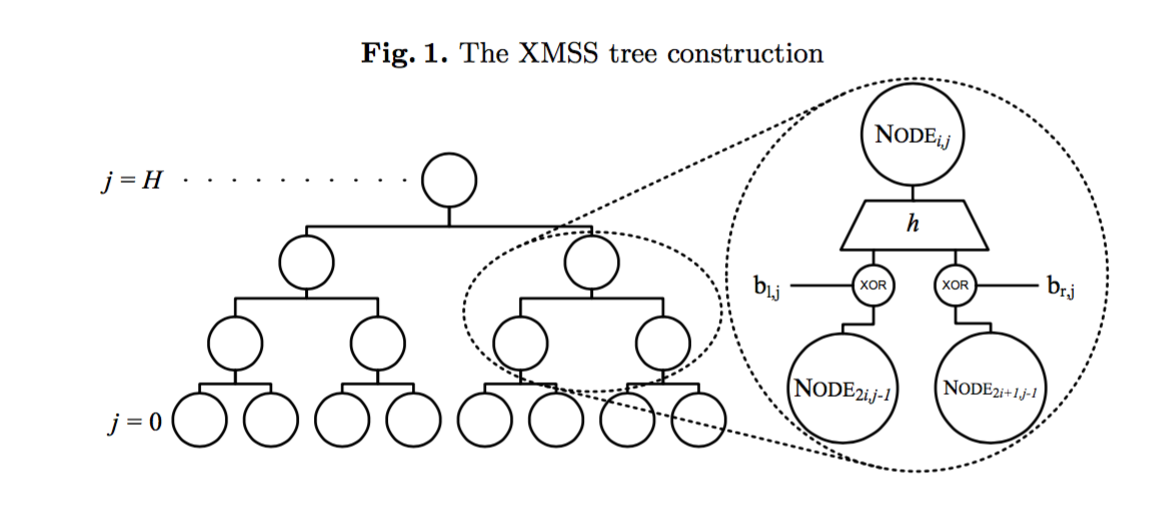
The eXtended Merkel Signature Scheme (XMSS), a hash-bashed digital signature scheme that is based on existing descriptions in scientific literature. There are three types of signatures specified for Winternitz One-Time Signature Plus (WOTS+), a one-time signature scheme; XMSS, a single-tree scheme; and XMSS^MT, a multi-tree variant of XMSS. Both XMSS and XMSS^MT use WOTS+ as a main bulding block. XMSS provides cryptographic digital signatures without relying on the conjectured hardness of mathematical problems. Instead, it is proven that it only relies on the properties of cryptographic hash functions. XMSS provides strong security guarantees and is even secure when the collison resistance of the underlying hash function is broken. Its is suitable for compact implementations, is relatively simple to implement, and naturally resists side-channel attacks. Unlike most other signature systems, hash-based signatures can so far withstand known attacks using quantum computers
The xmss_algorithm_t used to create the security association is sufficient to determine all other initial parameters for the desired XMSS signatures
Supported XMSS Parameters
| Name | H | m | h | type value |
|---|---|---|---|---|
| XMSS_SHA2_10_256 | SHA256 | 32 | 10 | 0x00000001 |
| XMSS_SHA2_16_256 | SHA256 | 32 | 16 | 0x00000002 |
| XMSS_SHA2_20_256 | SHA256 | 32 | 20 | 0x00000003 |
| XMSS_SHA2_10_192 | SHA256 | 24 | 10 | 0x0000000D |
| XMSS_SHA2_16_192 | SHA256 | 24 | 16 | 0x0000000E |
| XMSS_SHA2_20_192 | SHA256 | 24 | 20 | 0x0000000F |
| XMSS_SHAKE256_10_256 | SHAKE256 | 32 | 10 | 0x00000010 |
| XMSS_SHAKE256_16_256 | SHAKE256 | 32 | 16 | 0x00000011 |
| XMSS_SHAKE256_20_256 | SHAKE256 | 32 | 20 | 0x00000012 |
| XMSS_SHAKE256_10_192 | SHAKE256 | 24 | 10 | 0x00000013 |
| XMSS_SHAKE256_16_192 | SHAKE256 | 24 | 16 | 0x00000014 |
| XMSS_SHAKE256_20_192 | SHAKE256 | 24 | 20 | 0x00000015 |
Supported XMSS^MT Parameters
| Name | H | m | h | d | type value |
|---|---|---|---|---|---|
| XMSSMT_SHA2_20_2_256 | SHA256 | 32 | 20 | 2 | 0x00000001 |
| XMSSMT_SHA2_20_4_256 | SHA256 | 32 | 20 | 4 | 0x00000002 |
| XMSSMT_SHA2_40_2_256 | SHA256 | 32 | 40 | 2 | 0x00000003 |
| XMSSMT_SHA2_40_4_256 | SHA256 | 32 | 40 | 4 | 0x00000004 |
| XMSSMT_SHA2_40_8_256 | SHA256 | 32 | 40 | 4 | 0x00000005 |
| XMSSMT_SHA2_60_3_256 | SHA256 | 32 | 60 | 3 | 0x00000006 |
| XMSSMT_SHA2_60_6_256 | SHA256 | 32 | 60 | 6 | 0x00000007 |
| XMSSMT_SHA2_60_12_256 | SHA256 | 32 | 60 | 12 | 0x00000008 |
| XMSSMT_SHA2_20_2_192 | SHA256 | 32 | 20 | 2 | 0x00000021 |
| XMSSMT_SHA2_20_4_192 | SHA256 | 32 | 20 | 4 | 0x00000022 |
| XMSSMT_SHA2_40_2_192 | SHA256 | 32 | 40 | 2 | 0x00000023 |
| XMSSMT_SHA2_40_4_192 | SHA256 | 32 | 40 | 4 | 0x00000024 |
| XMSSMT_SHA2_40_8_192 | SHA256 | 32 | 40 | 4 | 0x00000025 |
| XMSSMT_SHA2_60_3_192 | SHA256 | 32 | 60 | 3 | 0x00000026 |
| XMSSMT_SHA2_60_6_192 | SHA256 | 32 | 60 | 6 | 0x00000027 |
| XMSSMT_SHA2_60_12_192 | SHA256 | 32 | 60 | 12 | 0x00000028 |
| XMSSMT_SHAKE256_20_2_256 | SHAKE256 | 32 | 20 | 2 | 0x00000029 |
| XMSSMT_SHAKE256_20_4_256 | SHAKE256 | 32 | 20 | 4 | 0x0000002A |
| XMSSMT_SHAKE256_40_2_256 | SHAKE256 | 32 | 40 | 2 | 0x0000002B |
| XMSSMT_SHAKE256_40_4_256 | SHAKE256 | 32 | 40 | 4 | 0x0000002C |
| XMSSMT_SHAKE256_40_8_256 | SHAKE256 | 32 | 40 | 4 | 0x0000002D |
| XMSSMT_SHAKE256_60_3_256 | SHAKE256 | 32 | 60 | 3 | 0x0000002E |
| XMSSMT_SHAKE256_60_6_256 | SHAKE256 | 32 | 60 | 6 | 0x0000002F |
| XMSSMT_SHAKE256_60_12_256 | SHAKE256 | 32 | 60 | 12 | 0x00000030 |
| XMSSMT_SHAKE256_20_2_192 | SHAKE256 | 32 | 20 | 2 | 0x00000031 |
| XMSSMT_SHAKE256_20_4_192 | SHAKE256 | 32 | 20 | 4 | 0x00000032 |
| XMSSMT_SHAKE256_40_2_192 | SHAKE256 | 32 | 40 | 2 | 0x00000033 |
| XMSSMT_SHAKE256_40_4_192 | SHAKE256 | 32 | 40 | 4 | 0x00000034 |
| XMSSMT_SHAKE256_40_8_192 | SHAKE256 | 32 | 40 | 4 | 0x00000035 |
| XMSSMT_SHAKE256_60_3_192 | SHAKE256 | 32 | 60 | 3 | 0x00000036 |
| XMSSMT_SHAKE256_60_6_192 | SHAKE256 | 32 | 60 | 6 | 0x00000037 |
| XMSSMT_SHAKE256_60_12_192 | SHAKE256 | 32 | 60 | 12 | 0x00000038 |

For API Documentation:
- See also
- ProtocolPP::jxmssa
- ProtocolPP::jxmss
For Additional Documentation:
The source code contained or described herein and all documents related to the source code (herein called "Material") are owned by John Peter Greninger and Sheila Rocha Greninger. Title to the Material remains with John Peter Greninger and Sheila Rocha Greninger. The Material contains trade secrets and proprietary and confidential information of John Peter Greninger and Sheila Rocha Greninger. The Material is protected by worldwide copyright and trade secret laws and treaty provisions. No part of the Material may be used, copied, reproduced, modified, published, uploaded, posted, transmitted, distributed, or disclosed in any way without prior express written consent of John Peter Greninger and Sheila Rocha Greninger (both are required)
No license under any patent, copyright, trade secret, or other intellectual property right is granted to or conferred upon you by disclosure or delivery of the Materials, either expressly, by implication, inducement, estoppel, or otherwise. Any license under such intellectual property rights must be express and approved by John Peter Greninger and Sheila Rocha Greninger in writing
Licensing information can be found at www.protocolpp.com/license with use of the binary forms permitted provided that the following conditions are met:
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution
- Any and all modifications must be returned to John Peter Greninger at GitHub.com https://github.com/jpgreninger/protocolpp for evaluation. Inclusion of modifications in the source code shall be determined solely by John Peter Greninger. Failure to provide modifications shall render this license NULL and VOID and revoke any rights to use of Protocol++®
- Commercial use (incidental or not) requires a fee-based license obtainable at www.protocolpp.com/shop
- Academic or research use requires prior written and notarized permission from John Peter and Sheila Rocha Greninger
Use of the source code requires purchase of the source code. Source code can be purchased at www.protocolpp.com/shop
- US Copyrights at https://www.copyright.gov/
- TXu002059872 (Version 1.0.0)
- TXu002066632 (Version 1.2.7)
- TXu002082674 (Version 1.4.0)
- TXu002097880 (Version 2.0.0)
- TXu002169236 (Version 3.0.1)
- TXu002182417 (Version 4.0.0)
- TXu002219402 (Version 5.0.0)
- TXu002272076 (Version 5.2.1)
The name of its contributor may not be used to endorse or promote products derived from this software without specific prior written permission and licensing
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDER AND CONTRIBUTOR "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE
The documentation for this class was generated from the following file:
- jxmss/include/jxmssa.h